diagnose test application lted
Firmware – FortiOS: 5.0 5.2 5.4
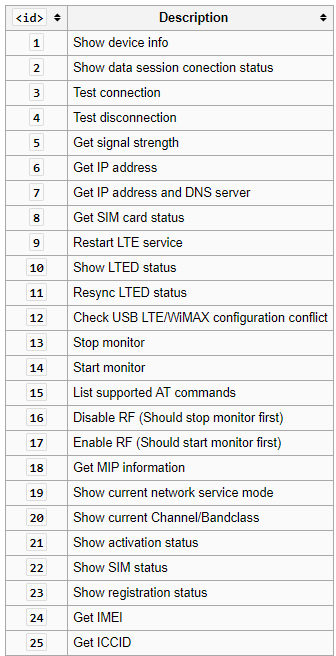
This is the LTE modem diagnose command.
Syntax
diagnose test application lted
Options
diagnose test application autodM/h3>
Firmware – FortiOS: 6.0.1<
This command is used to display information about your automation stitches. There are 3 different options.
Syntax
diagnose firewall test application autod {1 | 2 | 3}
Options
1 Toggles between enabling and disabling log dumping
2 Displays settings for all automation stitches
3 Display the history for all your automation stitches
Example(s)
autod 1
diagnose test application autod 1
autod log dumping is enabled
diagnose test application autod 1
autod log dumping is disabled
autod logs dumpping summary:
autod dumped total:0 logs, num of logids:0
autod 2
diagnose test application autod 2
csf: enabled root:yes
total stitches activated: 2
stitch: Compromised-IP-Banned
destinations: all
trigger: Compromised-IP-Banned
actions:
Compromised-IP-Banned_ban-ip type:ban-ip interval:0
stitch: HA-failover
destinations: HA-failover_ha-cluster_25;
trigger: HA-failover
actions:
HA-failover_email type:email interval:0
subject: HA Failover
mailto:admin@example.com:
autod 3
diagnose test application autod 3
stitch: Compromised-IP-Banned
local hit: 0 relayed to: 0 relayed from: 0
last trigger:Wed Dec 31 20:00:00 1969
last relay:Wed Dec 31 20:00:00 1969
actions:
Compromised-IP-Banned_ban-ip:
done: 0 relayed to: 0 relayed from: 0
last trigger:Wed Dec 31 20:00:00 1969
last relay:Wed Dec 31 20:00:00 1969
stitch: HA-failover
local hit: 1 relayed to: 1 relayed from: 1
last trigger:Thu May 24 11:35:22 2018
last relay:Thu May 24 11:35:22 2018
actions:
HA-failover_email:
done: 1 relayed to: 1 relayed from: 1
last trigger:Thu May 24 11:35:22 2018
last relay:Thu May 24 11:35:22 2018
diagnose test application csfd
Firmware FortiOS: 5.4 5.6
In 5.6
Two additional test levels have been added to the diagnose test application csfd command in order to dump some additional information about timers, file handlers status and received MAC addresses to the HA master.
Syntax
diag test app csfd
Options
11
40
diagnose test application dhcprelay
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application dhcprelay < Integer Test level. > — DHCP relay daemon
diagnose test application dsd
Firmware – FortiOS: 5.0 5.2 5.4
This command is used to dsiplay DLP Statistics daemon.
Syntax
diagnose test application dsd < Integer Test level >
Integer Level
1 This menu
2 Display memory usage
3 Display malloced devices
diagnose test application fcnacd
Firmware – FortiOS: 6.0
Used to print out the number of children created to make EMS REST API calls
Syntax
diagnose test application fcnacd
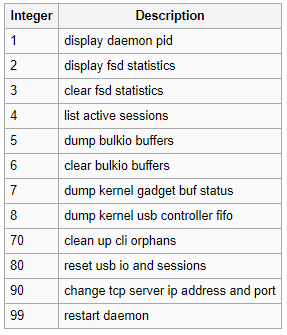
diagnose test application fsd
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application fsd < Integer Test level. > — FortiExplorer daemon
Command
diagnose test application fsd 2
Output
Seconds since last reset: 1056941
usb bulk IO: tx 27484534, rx 5415092, blocks 451, queues 1024, total 15690
utp cmd: total 88, dropped 0 (keepalive 0, disc 0)
::rx cmds queued/attempted 0/0
UTP sessions: active 1 max 1 total 25
CLI sessions: active 0 max 0 total 0
HTTP sessions: active 0 max 7 total 838
TELNET sessions: active 1 max 1 total 1
diagnose test application ipldbd
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application ipldbd < Integer Test level. > — IP load balancing daemon.
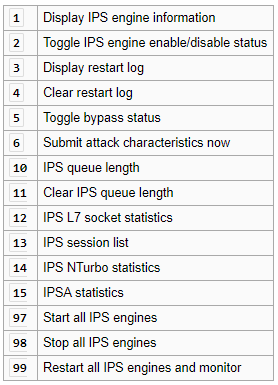
diagnose test application ipsengine
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application ipsengine < Integer Test level. > — ips sensor
Options
The
Command
diagnose test application ipsmonitor 1
Output
pid = 66, engine count = 1
0 – pid:82:82 cfg:1 master:0 run:1
Command
diagnose test application ipsmonitor 3
Output
ipsengine exit log:
pid = 75(cfg), duration = 1 (s) at Thu Mar 23 17:49:23 2017
code = 11, reason: manual
diagnose test application ipsufd
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application ipsufd < Integer Test level. > — IPS urlfilter daemon
Integer Levels
1 show all domain name & ip entries
2 show all unresolved domain names
3 show summary statistics
4 verify routing table entries
44 verify routing table entries (verbose)
5 show all join table entries
diagnose test application pptpcd
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application pptpcd < Integer Test level. > — PPTP client
diagnose test application proxyacceptor
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application proxyacceptor < Integer Test level > — Proxy acceptor
Proxy Acceptor Test Usage
1 Dump memory usage
4 Display acceptor stats
99 Restart proxy acceptor
diagnose test application smtp
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application smtp < Integer Test level. > — SMTP proxy
SMTP Proxy Test Usage
2 – Drop all connections
4 – Display connection stat
44 – Display info per connection
444 – Display connections per state
4444 – Display per vdom stats
diagnose test application uploadd
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application uploadd < Integer Test level > — Upload daemon.
Test Levels for uploadd
1 – show stats
99 – restart
Command
diagnose test application uploadd 1
Output
vdom_admin:0
have_disk:0
in_ha_mode:0
ha_vfid:1
mgmt_vfid:0
ha_direct:0
hamgmt_vfid:-1
global:
vdom:0-root
diagnose test application wccpd
Description
This command is used to display information about WCCP operations.
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test application wccpd < Integer Test level >
1 – Display WCCP stats
2 – Display WCCP config
3 – Display WCCP cache servers
4 – Display WCCP services
5 – Display WCCP assignment
Example(s)
Sample output from a successful WCCP connection.
Command
diag test application wccpd 3
Output
service-0 in vdom-root: num=1, usable=1
cache server ID:
len=44, addr=172.16.78.8, weight=4135, status=0
rcv_id=6547, usable=1, fm=1, nq=0, dev=3(k3),
to=192.168.11.55
ch_no=0, num_router=1:
192.168.11.55
Sample output from the same command from an unsuccessful WCCP connection (because of a service group password mismatch)
Output
service-0 in vdom-root: num=0, usable=0
diag debug application wccpd -1
Sample output:
wccp_on_recv()-98: vdom-root recv: num=160, dev=3(3),
172.16.78.8->192.168.11.55
wccp2_receive_pkt()-1124: len=160, type=10, ver=0200,
length=152
wccp2_receive_pkt()-1150: found component:t=0, len=20
wccp2_receive_pkt()-1150: found component:t=1, len=24
wccp2_receive_pkt()-1150: found component:t=3, len=44
wccp2_receive_pkt()-1150: found component:t=5, len=20
wccp2_receive_pkt()-1150: found component:t=8, len=24
wccp2_check_security_info()-326: MD5 check failed
diagnose test authserver local
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test authserver local < arg please input args > — Test local user. {5.0}
diagnose test authserver pop3
Firmware – FortiOS: 5.0 5.2 5.4
This command is used to test POP3 server.
Syntax
diagnose test authserver pop3 < arg please input args >
Options
Arguments
diagnose test authserver radius-direct
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test authserver radius-direct
diagnose test authserver tacacs+
Firmware – FortiOS: 5.0 5.2 5.4
Syntax
diagnose test authserver tacacs+
diagnose test app miglogd 106
Firmware – FortiOS: 5.6
This command is used to dump out the service name cache kept by the miglogd daemon for each individual VDOM.
Syntax
diagnose test app miglogd 106
Command
diagnose test app miglogd 106
Output
This output has been edited. Only the first 5 of each grouping has been included.
tcp
port(0), name(NONE)
port(21), name(FTP)
port(22), name(SSH)
port(23), name(TELNET)
port(25), name(SMTP)
udp
port(53), name(DNS)
port(67–68), name(DHCP)
port(69), name(TFTP)
port(88), name(KERBEROS)
port(111), name(ONC-RPC) extra: (ONC-RPC) (NFS)
icmp
port(1), name(test)
port(8), name(PING)
port(13), name(TIMESTAMP)
port(15), name(INFO_REQUEST)
port(17), name(INFO_ADDRESS)
general
prot(6), port(4300), name(example.com_Webadmin)
prot(6), port(5060), name(SIP)
prot(6), port(5190–5194), name(AOL)
prot(6), port(5631), name(PC-Anywhere)
prot(6), port(5900), name(VNC)
service names:
WINFRAME,DNS,DCE-RPC,H323,RLOGIN,IRC,UUCP,example.com_Webadmin,HTTPS,WAIS,FINGER,REXEC,
RAUDIO,SNMP,TIMESTAMP,RADIUS-OLD,DHCP,AOL,MGCP,SMTPS,INFO_REQUEST,HTTP,SCCP,SOCKS,PPTP,
ONC-RPC,NNTP,SMTP,QUAKE,PC-Anywhere,TFTP,NONE,SSH,RSH,IMAPS,LDAP_UDP,SIP,RIP,PING,PING6,
X-WINDOWS,SMB,SAMBA,TRACEROUTE,NFS,WINS,L2TP,IMAP,GOPHER,SIP-MSNmessenger,SYSLOG,DHCP6,
TELNET,LDAP,MS-SQL,MMS,KERBEROS,SQUID,NTP,FTP,CVSPSERVER,test,AFS3,POP3,Internet-Locator-
Service,
service groups:
Email Access(DNS,IMAP,IMAPS,POP3,POP3S,SMTP,SMTPS,)
Windows AD(DCE-RPC,DNS,KERBEROS,LDAP,LDAP_UDP,SAMBA,SMB,)
Web Access(DNS,HTTP,HTTPS,)
Exchange Server(DCE-RPC,DNS,HTTPS,)
policies involving mutiple service definitions:
